Trezor Hardware Wallet: The Key to Ultimate Cryptocurrency Security
In the fast-evolving world of cryptocurrency, securing your digital assets is more important than ever. Every day, investors and traders face risks from hackers, scams, and malware targeting their valuable crypto holdings. The solution to these risks lies in using a trusted and proven device: the Trezor hardware wallet.
Cryptocurrencies are reshaping the financial world, offering unparalleled freedom, privacy, and control. However, along with these opportunities come real risks. Cyberattacks, phishing scams, and exchange hacks are becoming more sophisticated every day.
For anyone serious about protecting their investments, using a Trezor hardware wallet is not just a choice — it is a necessity.
Trezor has established itself as a pioneer in the world of hardware wallets. With robust security features, intuitive software integration, and a reputation for transparency, the Trezor hardware wallet provides everything needed to keep your digital assets safe from threats.
This guide will walk you through everything you need to know about why the Trezor hardware wallet is the best option available today.
What is the Trezor Hardware Wallet?
The Trezor hardware wallet is a physical device that secures your cryptocurrency by keeping your private keys completely offline.
Unlike hot wallets or exchange-based wallets, which are constantly connected to the internet and exposed to hacking attempts, Trezor isolates your sensitive information from online risks.
By using a Trezor hardware wallet, you gain full ownership and control of your digital assets. You do not need to rely on third parties, and you are protected even if your computer is infected with malware.
The importance of owning your private keys cannot be overstated. With a Trezor device, the only way your crypto can be accessed is through your physical control of the device and your recovery seed.
How to Get Started with Trezor: Setup and Installation
Setting up your Trezor hardware wallet is straightforward. Once you purchase your device, the first step is visiting Trezor.io/start to begin the setup process.
The setup includes:
-
Installing Trezor Suite, the secure application to manage your assets.
-
Installing Trezor Bridge, which enables secure communication between your Trezor hardware wallet and your computer.
-
Creating your recovery seed, a sequence of 12, 18, or 24 words that acts as a backup for your wallet.
One of the most critical moments during setup is writing down your recovery seed. It must be stored securely offline, preferably in a physical form like a piece of paper or a metal backup solution.
After completing the setup, you can start receiving and sending cryptocurrencies securely through Trezor Suite.
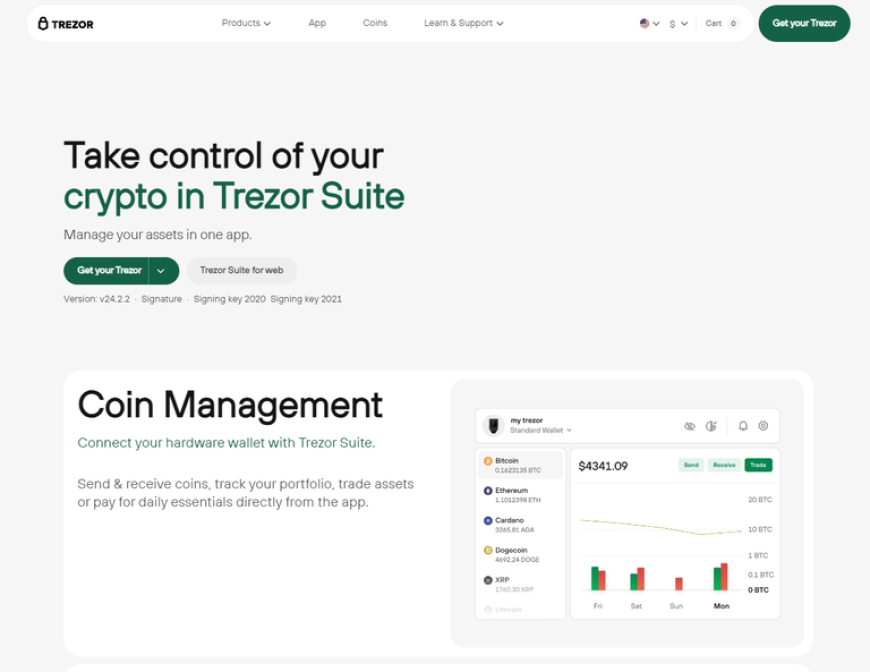
Trezor Suite: Managing Your Crypto with Confidence
Trezor Suite is designed to offer a seamless and highly secure environment for managing your cryptocurrencies. Available as a desktop application, Trezor Suite allows users to:
-
Send and receive cryptocurrencies
-
Monitor portfolio performance
-
Buy, sell, and exchange crypto directly
-
Use privacy-enhancing features like CoinJoin and Tor integration
Trezor Suite is regularly updated to provide the latest security improvements and usability features. Its user-friendly interface makes it easy for both beginners and advanced users to operate their Trezor hardware wallet efficiently.
Unlike many web-based wallets, Trezor Suite ensures that your private keys never touch an online server, reinforcing your protection at all times.
Trezor Bridge: The Secure Link Between Your Device and Browser
Trezor Bridge is a small piece of software that allows your Trezor hardware wallet to interact securely with your computer and browsers.
It operates in the background, making sure that your device can safely communicate with Trezor Suite and web apps without exposing sensitive data.
Trezor Bridge eliminates the need for browser extensions that can often be security risks themselves. Regular updates to Trezor Bridge ensure compatibility with the latest browser and system versions, making it a critical component of the Trezor experience.
Installing and updating Trezor Bridge is a simple yet important step to guarantee your crypto management remains secure.
Trezor Staking: Putting Your Assets to Work
Cryptocurrency staking is a method of earning rewards by participating in network validation processes. With Trezor staking, you can safely stake supported coins while retaining control of your private keys.
Although native staking options are somewhat limited within Trezor Suite at the moment, Trezor users can connect their hardware wallets to trusted third-party platforms that allow for secure staking operations.
This approach offers a great way to grow your crypto portfolio without sacrificing the security benefits of using a Trezor hardware wallet.
Popular staking assets like Cardano (ADA) and Tezos (XTZ) can be staked securely while keeping your funds protected inside your Trezor device.
How Trezor Compares to Ledger Hardware Wallets
The Ledger hardware wallet is another major player in the market. Available through Ledger.com/start, Ledger wallets provide excellent security features as well.
However, there are some important differences between Trezor and Ledger devices.
Trezor is fully open-source, allowing complete transparency into its codebase. Ledger, by contrast, uses a combination of open-source and closed-source software, which means users must place some level of trust in their closed components.
Trezor hardware wallets connect exclusively through USB, reducing potential wireless attack vectors. Some Ledger models, like the Nano X, offer Bluetooth connectivity, making them more convenient for mobile use but introducing a small additional risk.
When it comes to software, Trezor Suite offers advanced privacy tools that are not found in Ledger Live, Ledger’s equivalent management app.
Choosing between the two often comes down to personal preferences. Those who prioritize open-source transparency and minimal online exposure often prefer Trezor, while those seeking strong mobile integration might lean toward Ledger.
Why You Should Trust Trezor for Your Crypto Security
The Trezor hardware wallet has a long and trusted history in the cryptocurrency community. Its focus on security, transparency, and user empowerment makes it an excellent choice for both beginners and seasoned investors.
With Trezor Suite providing a secure and intuitive interface, Trezor Bridge ensuring seamless communication, and the ability to engage in Trezor staking, users get a complete and secure environment for managing digital assets.
By taking the crucial step of moving your crypto into cold storage with a Trezor hardware wallet, you are dramatically reducing your risk exposure. You are no longer depending on centralized exchanges or online wallets that can be compromised or shut down.
Final Thoughts
As cryptocurrencies continue to gain mainstream acceptance, the need for strong, reliable security will only grow.
The Trezor hardware wallet stands out as a simple yet powerful tool for anyone looking to protect their digital wealth.
From easy setup through Trezor.io/start, to daily management with Trezor Suite and secure communication via Trezor Bridge, everything about the Trezor experience is designed for peace of mind.
Adding staking capabilities only enhances its appeal for long-term holders.
When it comes to safeguarding your financial freedom, choosing a trusted name like Trezor is one of the smartest decisions you can make.
Take control of your crypto today — your future self will thank you.
Read more :
| Trezor.io/start | Trezor.io/start | Trezor bridge | Trezor suite | Trezor staking | Trezor.io/start | Trezor suite | Trezor Hardware Wallet | Trezor.io/start | Ledger hardware wallet | Ledger.com/start | Trezor staking | Trezor suite | Trezor Hardware Wallet | Ledger hardware wallet |

 ianbell9625
ianbell9625